CyberML™ for Cybersecurity Architecture & Design MODSIM
CyberML FAQ: What is CyberML?
The CyberML architecture patterns model library specifies recursive analysis, design, and architecture patterns that are intended to be applied to Network diagrams during Low-Level System Design (cf. System Analysis and High-Level System Design), during with software and hardware components are deployed to network nodes.
The CyberML can be customized to support a broad range of problem domains ranging from aerospace and automotive to healthcare and finance.
* network nodes (computers, NICs, repeaters, hubs, bridges, switches, routers, modems, gateways, etc.)
* network communication protocols (TCP/IP, DHCP, DNS, FTP, HTTP, IMAP, SMTP, SMS, MMS, etc.)
* network connections between nodes using specific protocols
* network topologies among nodes (point-to-point, bus, star, ring or circular, mesh, tree, daisy chain, hybrid)
* cybersecurity devices (firewalls, Intrusion Detection/Protection Systems [IDS/IPS], encryption/decryption devices, etc.)
* secure network communication protocols (SSL, TLS, HTTPS, etc.)
* strong encryption techniques (End-to-End Encryption [E2EE], Zero-Knowledge Proofs (ZKP), blockchains, etc.)
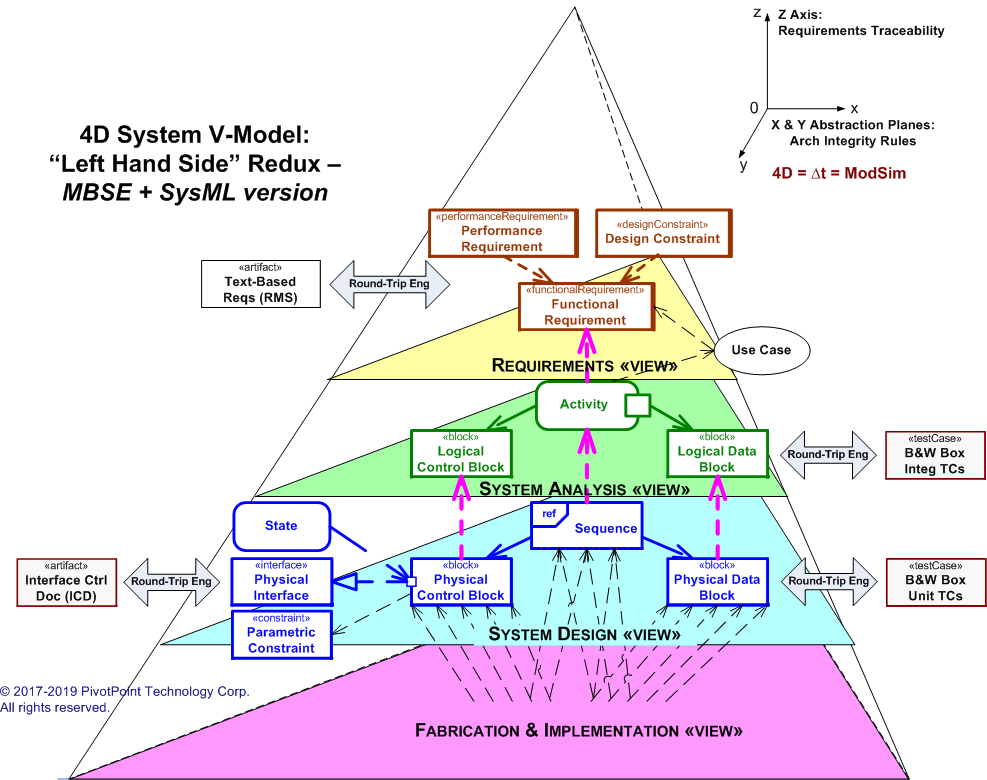
The CyberML model library specifies recursive analysis, design and architecture patterns that can be applied during the full System Development Life Cycle (SDLC) on "both sides" of the System V-Model (a.k.a. System Vee Model). When used with a pragmatic "Agile" subset of either UML 2 or SysML 1.x, these recursive analysis, design and architecture patterns facilitate scalable traceability on the "left side" of the System-V Model, and scalable Verification & Validation (V&V) on the "right side" of the System-V Model.
The CyberML can be customized to support emerging Cybersecurity Framework standards, such as the NIST Cybersecurity Framework (NIST Special Publication 800-37), DoD Risk Management Framework (RMF), and ISO/IEC 27000.
Alternative FAQ Phrasings: What is a cybersecurity architecture? | What is a cyber security architecture? | What is a cyber architecture?
The term cybersecurity architecture (or cyber architecture for short) is commonly used to describe computer network architectures that include and emphasize cybersecurity features, such as cybersecurity devices (firewalls, Intrusion Detection/Protection Systems [IDS/IPS], encryption/decryption devices, etc.) and secure communication protocols (HTTPS, SSL, etc.).
In order to specify a cybersecurity architecture precisely and completely you should use a bona fide architecture modeling language (UML2, SysML, CyberML) to define the following network and security elements:
- network nodes (computers, NICs, repeaters, hubs, bridges, switches, routers, modems, gateways, etc.)
- network communication protocols (TCP/IP, DHCP, DNS, FTP, HTTP, IMAP, SMTP, SMS, MMS, etc.)
- network connections between nodes using specific protocols
- network topologies among nodes (point-to-point, bus, star, ring or circular, mesh, tree, daisy chain, hybrid)
- cybersecurity devices (firewalls, Intrusion Detection/Protection Systems [IDS/IPS], encryption/decryption devices, etc.)
- secure network communication protocols (SSL, TLS, HTTPS, etc.)
- strong encryption techniques (end-to-end encryption, Zero-knowledge Privacy (ZKP), blockchain, etc.)
- cybersecurity framework standards (NIST 800-37, DoD Instruction 8510.01, ISO IEC 27000)
For more information about cybersecurity architectures and how they differ from network architectures see:
- CyberSecurity FAQ - What is the purpose of cybersecurity architecture?
- CyberSecurity FAQ - What is the difference between cybersecurity and network architectures?
- CyberSecurity FAQ - What are the essential elements of cybersecurity architecture?
- CyberSecurity FAQ - What are the best practices for specifying cybersecurity architectures?
CyberML offers the following advantages over BUFD languages:
- Small & Lean → easier to learn and apply: When used with a pragmatic "Agile" (i.e., essential or "Lean") subset of UML 2 or SysML , SafetyML is relatively easy to learn and apply. If you already have a solid foundation and experience applying Agile UML 2 or SysML, you should be able to learn CyberML during a 2-4 day hands-on workshop.
- Supports recursive analysis, design and architecture patterns → scalable: The CyberML model library specifies recursive analysis, design and architecture patterns that can be applied during the full System Development Life Cycle (SDLC) on "both sides" of the System V-Model (a.k.a. System Vee Model). When used with a pragmatic "Agile" subset of either UML 2 or SysML 1.x, these recursive analysis, design and architecture patterns facilitate scalable traceability on the "left side" of the System-V Model, and scalable Verification & Validation (V&V) on the "right side" of the System-V Model.
- Compatibility & Portability → straightforward to implement in UML2/SysML compliant tools: Since CyberML is designed and implemented as a UML profile (UML dialect) and model library it is compatible with the UML and OMG SysML architecture modeling language standards, and can be implemented in popular visual modeling tools that comply with those standards.
- Expressibility & Precision → precise blueprints for safety-critical systems of arbitrary complexity: Since CyberML emphasizes precise basic constructs and powerful recursive patterns, a relatively small number of CyberML constructs can specify safety-critical systems of arbitrary complexity (systems-of-systems → systems → subsystems → ...).
- Simulation & Executability → easier to test and debug: CyberML can be simulated and executed (behavioral diagram simulation, parametric simulation and support Round-Trip Engineering) in those visual modeling tool implementations that support these features.
- Cybersecurity focus → emphasized throughout Agile SDLC: CyberML's cybersecurity constructs and recursive patterns are deeply integrated into the system architecture, analysis, design, implementation and V&V, so cybersecurity is treated critically throughout the Agile System Development Life Cycle, rather than being treated as secondary or tertiary importance.
CyberML + SysML Diagram Usage
When used by Cyber and Network Architects applying a Agile SysML subset, the CyberML commonly adds two new diagram types to extend the standard SysML diagram types (modulo Use Cases):
- Reused SysML Diagrams:
- Requirement
- Activity
- Block Definition
- Internal Block
- Parametric
- Sequence
- State Machine
- Package
- Diagrams added by CyberML:
- Network (for network topologies)
- Cybersecurity (for cybersecurity overlays on top of Network diagrams)
CyberML + UML 2 + SysML Diagram Usage
When used by Cyber and Network Architects applying an Agile UML 2 subset, the CyberML commonly adds ttwo new diagram types and the SysML Requirement diagram type to the UML 2 diagram types listed below:
- Reused SysML Diagram:
- Requirement
- Reused UML 2 Diagrams:
- Activity
- Class
- Composite Structure
- Sequence
- State Machine
- Package
- Diagram added by CyberML:
- Network (for network topologies)
- Cybersecurity (for cybersecurity overlays on top of Network diagrams)
- Model-Based Cybersecurity is an approach to traditional Cybersecurity which emphasizes a Network Architecture Model (NAM) specified with an architecture modeling language, such as UML 2 or SysML, as the primary work artifact for cybersecurity architectures and frameworks.
- AgileML™ (Agile Modeling Language™) for Agile Architecture & Design MODSIM applications
- CyberML™ (Cyber Modeling Language™) for Cybersecurity Architecture & Design MODSIM applications
- CryptoML™ (Crypto Modeling Language™) for Cryptoeconomic Architecture & Design MODSIM applications
- SafetyML™ (Safety Modeling Language™) for Safety-critical Architecture & Design MODSIM applications
If you are interested in learning how you can obtain early access to CyberML, check out the following FAQ on the PivotPoint web: